题目下载下来是一个dd.img,首先挂载磁盘:
mount dd.img /mnt/cdrom/
cd /mnt/cdrom/
文件如下:
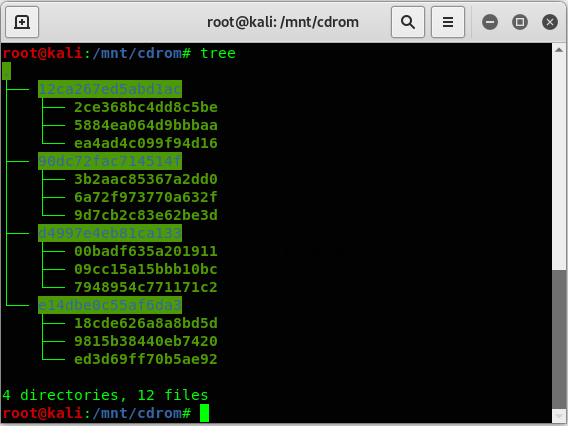
大部分都是让人不知道想表达什么的恶心文字,只有d4997e4eb81ca133文件夹下的7948954c771171c2文件不一样,通过file命令知道它是一个mp4文件。
打开图形文件夹(nautilus /mnt/cdrom/)可以看到这是一段视频,也是意义不明。strings磁盘会提示NTFS,但是我用ntfsstreamseditor对磁盘和磁盘内文件扫了一遍并没有发现什么Q Q
如果对题目文件使用tail命令会发现一串可疑的base64:
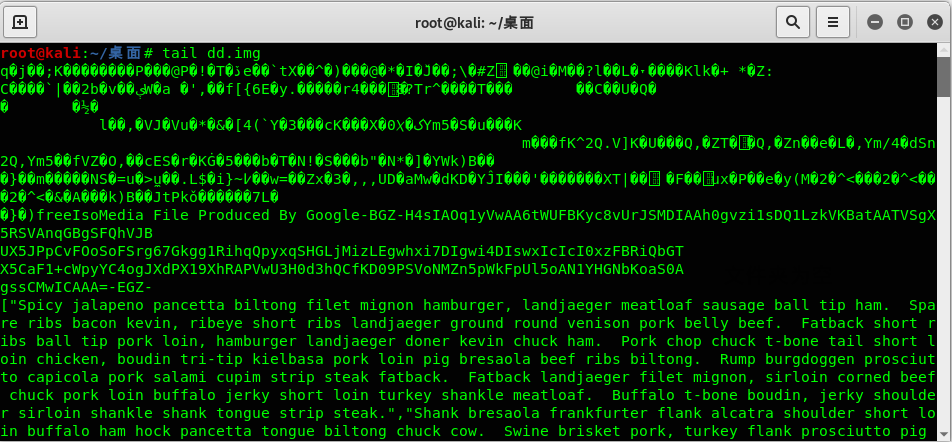
H4sIAOq1yVwAA6tWUFBKyc8vUrJSMDIAAh0gvzi1sDQ1LzkVKBatAATVSgX5RSVAnqGBgSFQhVJB
UX5JPpCvFOoSoFSrg67Gkgg1RihqQpyxqSHGLjMizLEgwhxi7DIgwi4DIswxIcIcI0xzFBRiQbGT
X5CaF1+cWpyYC4ogJXdPX19XhRAPVwU3H0d3hQCfKD09PSVoNMZn5pWkFpUl5oAN1YHGNbKoaS0A
gssCMwICAAA=
仔细看截图,base64的前(BGZ)后(EGZ),查阅了资料,这是一个gzip文件。
还原:
echo “H4sIAOq1yVwAA6tWUFBKyc8vUrJSMDIAAh0gvzi1sDQ1LzkVKBatAATVSgX5RSVAnqGBgSFQhVJBUX5JPpCvFOoSoFSrg67Gkgg1RihqQpyxqSHGLjMizLEgwhxi7DIgwi4DIswxIcIcI0xzFBRiQbGTX5CaF1+cWpyYC4ogJXdPX19XhRAPVwU3H0d3hQCfKD09PSVoNMZn5pWkFpUl5oAN1YHGNbKoaS0AgssCMwICAAA=” |base64 -d >file.gz
打开压缩包得到如下内容:
{ “door”: 20000, “sequence”: [ {“port”: 10010, “proto”: “UDP”}, {“port”: 10090, “proto”: “UDP”}, {“port”: 10020, “proto”: “TCP”}, {“port”: 10010, “proto”: “UDP”}, {“port”: 10060, “proto”: “TCP”}, {“port”: 10080, “proto”: “UDP”}, {“port”: 10010, “proto”: “UDP”}, {“port”: 10000, “proto”: “TCP”}, {“port”: 10000, “proto”: “UDP”}, {“port”: 10040, “proto”: “TCP”}, {“port”: 10020, “proto”: “UDP”} ], “open_sesame”: “GIMME THE FLAG PLZ…”, “seq_interval”: 10, “door_interval”: 5}

然后这里也学到了新知识点,超开心!
记笔记~记笔记~
上面那个文件是端口试探(port knocking):
如字面意思,类似‘敲门’,只是这里敲的是‘端口’,而且需要按照顺序‘敲’端口。如果敲击规则匹配,则可以让防火墙实时更改策略。从而达到开关防火墙的目的。
不过这道赛题已经关掉连不上了,马克一下国外师傅的脚本,还没有研究透,有待进一步学习:
#!/usr/bin/env python3
import time
import socket
import select
import json
class Knocker(object):
def __init__(self, ports_proto: list, delay=400, udp=False, host="127.0.0.1", timeout=200):
self.timeout = timeout / 1000
self.delay = delay / 1000
self.default_udp = udp
self.ports_proto = ports_proto
self.address_family, _, _, _, (self.ip_address, _) = socket.getaddrinfo(
host=host,
port=None,
flags=socket.AI_ADDRCONFIG
)[0]
def knock_it(self):
last_index = len(self.ports_proto) - 1
for i, port in enumerate(self.ports_proto):
use_udp = self.default_udp
if port.find(':') != -1:
port, protocol = port.split(':', 2)
if protocol == 'TCP':
use_udp = False
elif protocol == 'UDP':
use_udp = True
else:
error = 'WTF!'
raise ValueError(error.format(protocol))
s = socket.socket(self.address_family, socket.SOCK_DGRAM if use_udp else socket.SOCK_STREAM)
s.setblocking(False)
socket_address = (self.ip_address, int(port))
if use_udp:
print("Knocking port {} using UDP".format(port))
s.sendto(b'', socket_address)
else:
print("Knoocking port {} using TCP".format(port))
s.connect_ex(socket_address)
select.select([s], [s], [s], self.timeout)
s.close()
if self.delay and i != last_index:
time.sleep(self.delay)
if __name__ == '__main__':
host = "you-shall-not-pass.ctf.insecurity-insa.fr"
print("[?] Getting Data ...")
json_file = open("file", "r")
data = json.load(json_file)
open_sesame = data["open_sesame"]
ports_proto = [str(i["port"])+":"+i["proto"] for i in data["sequence"]]
print("[+] Knocking Ports now...")
Knocker(ports_proto, delay=900, host=host).knock_it()
time.sleep(1)
print("[?] Asking for Flag ...")
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, int(data["door"])))
except Exception as e:
print("[!] CONNECTION FAILED!!!, Port may not be opened")
else:
print("[+] DOOR OPENED")
s.send(open_sesame.encode())
try:
flag = s.recv(2014).decode()
print("Got flag: ", flag)
except Exception as e:
print("NOTHING")
finally:
s.close()
⚪参考:
https://omega-coder.ninja/post/inshack-you-shall-not-pass-forensics-330-writeup/
