AutoKey
看到这种题第一反应就是提取usb协议的数据:
tshark -r attachment.pcapng -T fields -e usb.capdata > usbdata.txt
去掉换行符,两两一个,用冒号分割,生成usbdata2.txt,如下:
import re
a = open("usbdata2.txt",'w+')
for line in open("usbdata.txt"):
result = re.sub(r"(?<=\w)(?=(?:\w\w)+$)", ":", line)
a.write(result)
print(result)

拿jio本翻译一下:
#!usr/bin/env python
#-*- coding:utf-8 -*-
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }
nums = []
keys = open('usbdata.txt')
for line in keys:
if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0':
continue
nums.append(int(line[6:8],16))
keys.close()
output = ""
for n in nums:
if n == 0 :
continue
if n in mappings:
output += mappings[n]
else:
output += '[unknown]'
print 'output :\n' + output
得到:
[unknown]A[unknown]UTOKEY”.DECIPHER'[unknown]MPLRVFFCZEYOUJFJKYBXGZVDGQAURKXZOLKOLVTUFBLRNJESQITWAHXNSIJXPNMPLSHCJBTYHZEALOGVIAAISSPLFHLFSWFEHJNCRWHTINSMAMBVEXO[DEL]PZE[DEL]IZ’
仔细看字符串开头,提示说“AUTOKEY”,但是autokey是需要密钥的,暂且不谈,先对字符串进行处理,把[unknown]A[unknown]UTOKEY”.删掉,然后把所有的[DEL]以及它前面的一个字符删掉,得:
MPLRVFFCZEYOUJFJKYBXGZVDGQAURKXZOLKOLVTUFBLRNJESQITWAHXNSIJXPNMPLSHCJBTYHZEALOGVIAAISSPLFHLFSWFEHJNCRWHTINSMAMBVEXPZIZ
查询了资料,get到了一个爆破密钥的脚本:
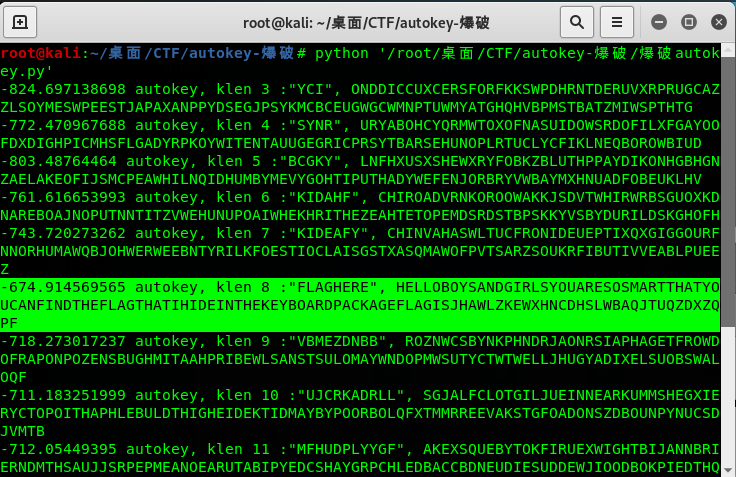
HELLOBOYSANDGIRLSYOUARESOSMARTTHATYOUCANFINDTHEFLAGTHATIHIDEINTHEKEYBOARDPACKAGEFLAGISJHAWLZKEWXHNCDHSLWBAQJTUQZDXZQPF
flag是第二行中间“FLAGIS”往后的部分:
flag{JHAWLZKEWXHNCDHSLWBAQJTUQZDXZQPF}
ppap
追踪流找到了非常可疑的这个:
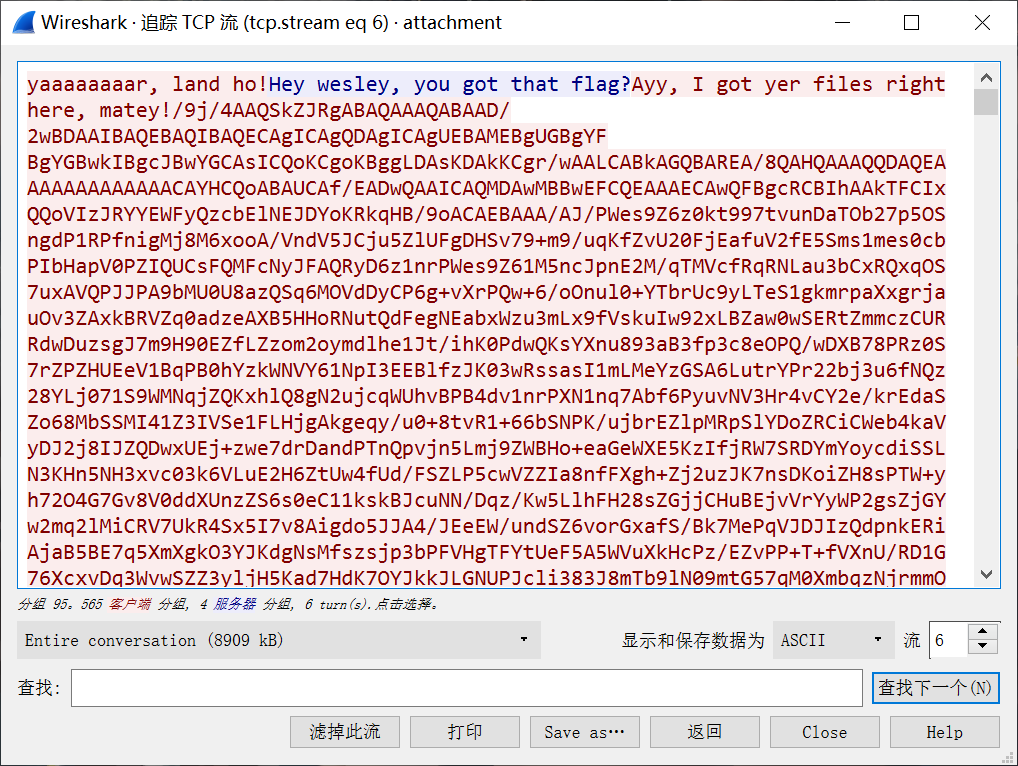
save,去掉开头和结尾,取base64这一段放在notepad++里解码保存为jpg,得到一张图片,然后拿binwalk取出文件其他的数据,得到一个加密的zip。
在这个网站可以解出zip密码:skullandcrossbones
https://passwordrecovery.io/zip-file-password-removal/
flag{b31Ng_4_P1r4tE_1s_4lR1GHT_w1Th_M3}
