借着这道题再次温习了Volatility。首先解压出来是一个很大的pcap流量包。
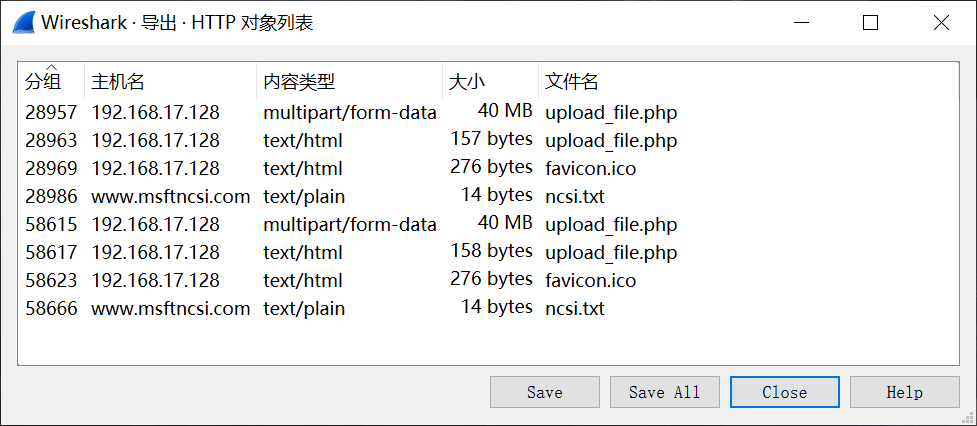
以防万一我做的时候都给导出来了qwq看那个最大的(upload_file.php)就可以啦。
因为太大了不能拿notepad++打开,我用010打开看了下,开头PK很明显是压缩包。
删除开头的这个:
-----------------------------154555628677 Content-Disposition: form-data; name="file"; filename="data.zip" Content-Type: application/octet-stream
删除结尾的这个:
-----------------------------154555628677 Content-Disposition: form-data; name="submit" Submit -----------------------------154555628677--
修改后缀得到一个压缩包。解压后得到一个名为data.vmem的文件。
接下来上Kali开始取证啦。以前的详细笔记:戳我
Volatility常用控件:戳我
volatility imageinfo -f data.vmem
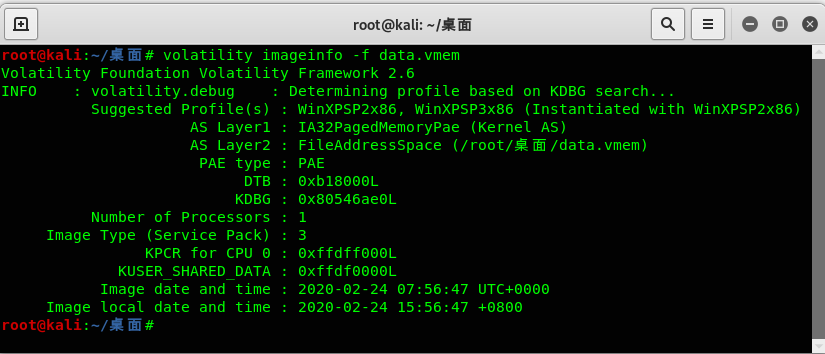
volatility psscan -f data.vmem –profile=WinXPSP2x86
对cmd控件进行提取:
volatility cmdscan -f data.vmem –profile=WinXPSP2x86
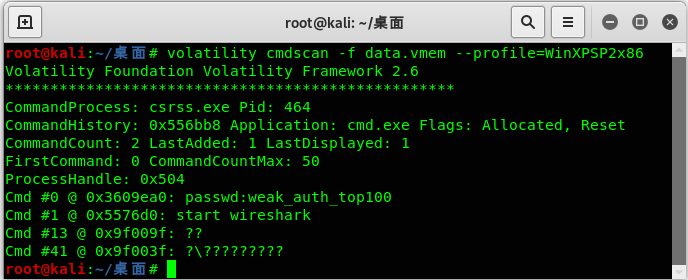
得到一个passwd:weak_auth_top100
搜索镜像中的所有文件(filescan),匹配关键字“flag”:
volatility filescan -f data.vmem –profile=WinXPSP2x86 | grep -E ‘flag’
得到一个flag.img,将其导出:
volatility -f data.vmem –profile=WinXPSP2x86 dumpfiles -Q 0x0000000001155f90 -n –dump-dir=./
binwalk一下它可以得到一个加密压缩包,解压密码就是上面得到的weak_auth_top100。
解压得到usbdata.txt,接下来就是个很普通的usb轨迹分析题了,上脚本:
#!/usr/bin/env python
import sys
import os
normalkeys = { 0x04:"a", 0x05:"b", 0x06:"c", 0x07:"d", 0x08:"e", 0x09:"f", 0x0A:"g", 0x0B:"h", 0x0C:"i", 0x0D:"j", 0x0E:"k", 0x0F:"l", 0x10:"m", 0x11:"n",0x12:"o", 0x13:"p", 0x14:"q", 0x15:"r", 0x16:"s", 0x17:"t", 0x18:"u",0x19:"v", 0x1A:"w", 0x1B:"x", 0x1C:"y", 0x1D:"z",0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"`", 0x33:";", 0x34:"'",0x35:"`", 0x36:",", 0x37:"." , 0x38:"/"}
shiftkeys = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"!", 0x1F:"@", 0x20:"#", 0x21:"$", 0x22:"%", 0x23:"^", 0x24:"&", 0x25:"*", 0x26:"(", 0x27:")", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"_", 0x2E:"+", 0x2F:"{", 0x30:"}", 0x31:"|", 0x32:"~", 0x33:":", 0x34:"\"",0x35:"~", 0x36:"<", 0x37:">", 0x38:"?" }
nums = []
shift_press = []
keys = open('usbdata.txt')
for line in keys:
shift_press.append(line[1])
nums.append(int(line[6:8],16))
keys.close()
output = ""
m = 0
for n in nums:
if n == 0 :
m += 1
continue
if n in shiftkeys:
if shift_press[m] == '2' : #shift is pressed
output += shiftkeys[n]
m += 1
elif shift_press[m] == '0' :
output += normalkeys[n]
m += 1
print 'output :\n' + output
运行得到flag。
